CloudFront – Restricting Access to an ALB
For web applications or other content served by an Application Load Balancer in Elastic Load Balancing, CloudFront can cache objects and serve them directly to users (viewers), reducing the load on the Application Load Balancer. However, if users can bypass CloudFront and access the Application Load Balancer directly, you don’t get these benefits.
However, you can configure Amazon CloudFront and the Application Load Balancer to prevent users from accessing the Application Load Balancer directly. This makes the Application Load Balancer accessible only through CloudFront, ensuring that you get the benefits of using CloudFront.
1. Custom HTTP headers
To prevent users from accessing your Application Load Balancer directly and allow access only through CloudFront, complete the following steps:
-
Configure a custom HTTP header for CloudFront.
-
Configure your Application Load Balancer to forward only requests that contain this custom HTTP header.
After you complete these steps, users can access your Application Load Balancer only through CloudFront.
2. Use the CloudFront managed prefix list
Available AWS managed prefix lists
The following services provide AWS managed prefix lists.
| AWS Service | Prefix List Name | Weight |
|---|---|---|
| Amazon CloudFront | com.amazonaws.global.cloudfront.origin-facing | 55 |
| Amazon DynamoDB | com.amazonaws.region.dynamodb |
1 |
| AWS Ground Station | com.amazonaws.global.groundstation | 5 |
| Amazon S3 | com.amazonaws.region.s3 |
1 |
AWS CLI View AWS Managed Prefix Lists
Use the describe-managed-prefix-lists command as follows.
aws ec2 describe-managed-prefix-lists --filters Name=owner-id,Values=AWS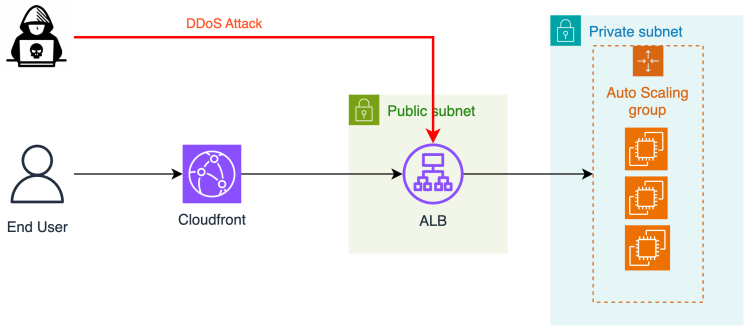
Comments